Unfortunately, besides ingenious and endless "Elon Musk/Donald Trump/Bill Gates XRP giveaways," cryptocurrency scammers sometimes launch sophisticated phishing attacks. The latest one targeted users of secure, high-end hardware wallet Ledger.
Scammers would do well not to mess with cypherpunks
Prominent cybersecurity expert Ryan Lackley, chief security officer of Tezos Foundation, reported that he received a malicious email regarding his Ledger wallet. This letter impersonated the Ledger team and informed crypto holders of a "security breach."
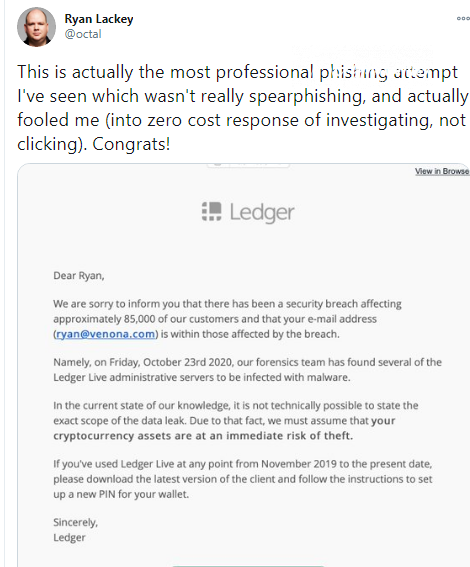
The suspicious letter warned Ledger users of a recently disclosed infection that allegedly plagued Ledger Live administrative servers. Scammers insist that customers' assets are "at immediate risks of theft."
Thus, the malefactors urged all Ledger Live users who have been active since November 2019 to download the latest version of its client and set up a new PIN for every wallet affected.
Lackley's Twitter audience noted that the entire text of the letter is written in an oddly wordy and old-fashioned manner:
In the current state of our knowledge...Your e-mail address is within those affected by the breach.
However, besides awkward and sloppy language, some technical red flags also surround this letter. A seasoned expert discovered the most obvious of them.
Always doublecheck the sender!
Eagle-eyed Lackley noticed that the letter was not sent by the official Ledger domain. The obscure "Ledger Support" domain was behind this spamming activity.
After checking the website in question via the publicly available "Who-is-service" that provides basic information about the owner and registrant of a domain name, Lackley found that scammers had registered it only one day before the "breach" was allegedly disclosed.
However, he added, using separate domains for support and other technical issues is not a crime but, if legit, both addresses should be well known. The rest of the scam was well designed: it did not ask for a seed phrase, PIN or password, which is common with "average" scams.
Lackley admitted that this phishing campaign is definitely run by professionals:
...It's 1) better than any phishing campaign I've seen before 2) better than a lot of actual breach notification emails I've received (esp from smaller, non-US, etc. companies).
As covered by CryptoComes, in July the malefactors launched a fake email newsletter impersonating the Coindesk crypto media outlet. They invited all readers to participate in "XRP reallocation," allegedly launched by Ripple Inc.